
Opcode Sequences As Representation of Executables For Data-Mining-Based Unknown Malware Detection (Elsevier-2013) PDF | PDF | Cross Validation (Statistics) | Machine Learning

Opcode Sequences As Representation of Executables For Data-Mining-Based Unknown Malware Detection (Elsevier-2013) PDF | PDF | Cross Validation (Statistics) | Machine Learning
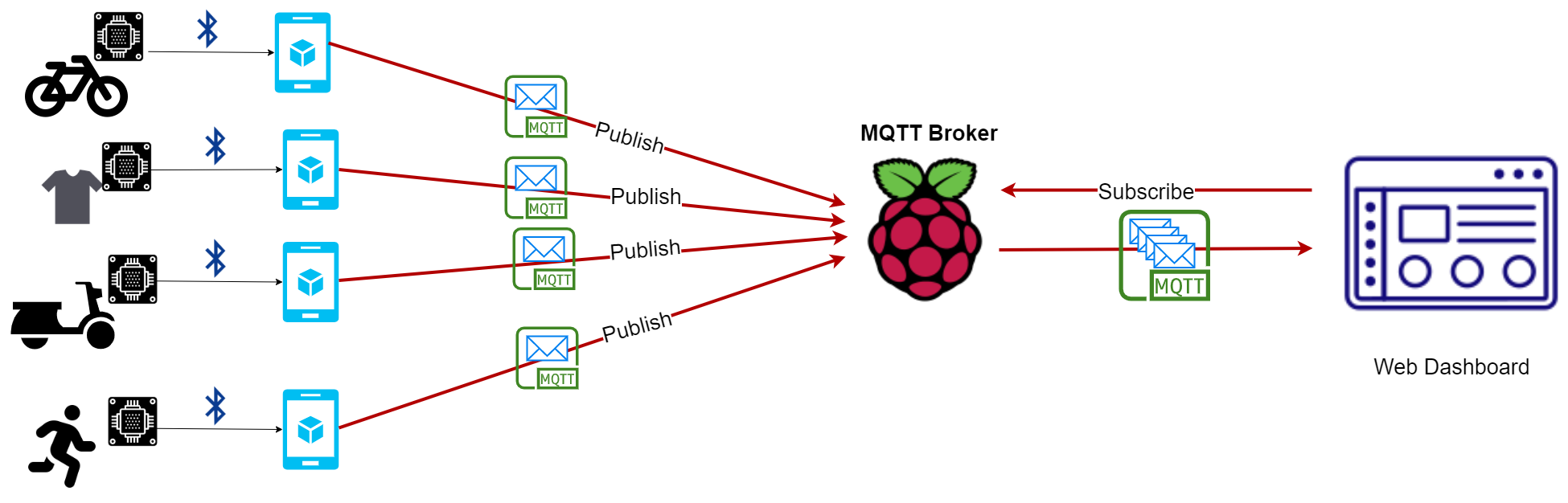
Future Internet | Free Full-Text | Open-Source MQTT-Based End-to-End IoT System for Smart City Scenarios
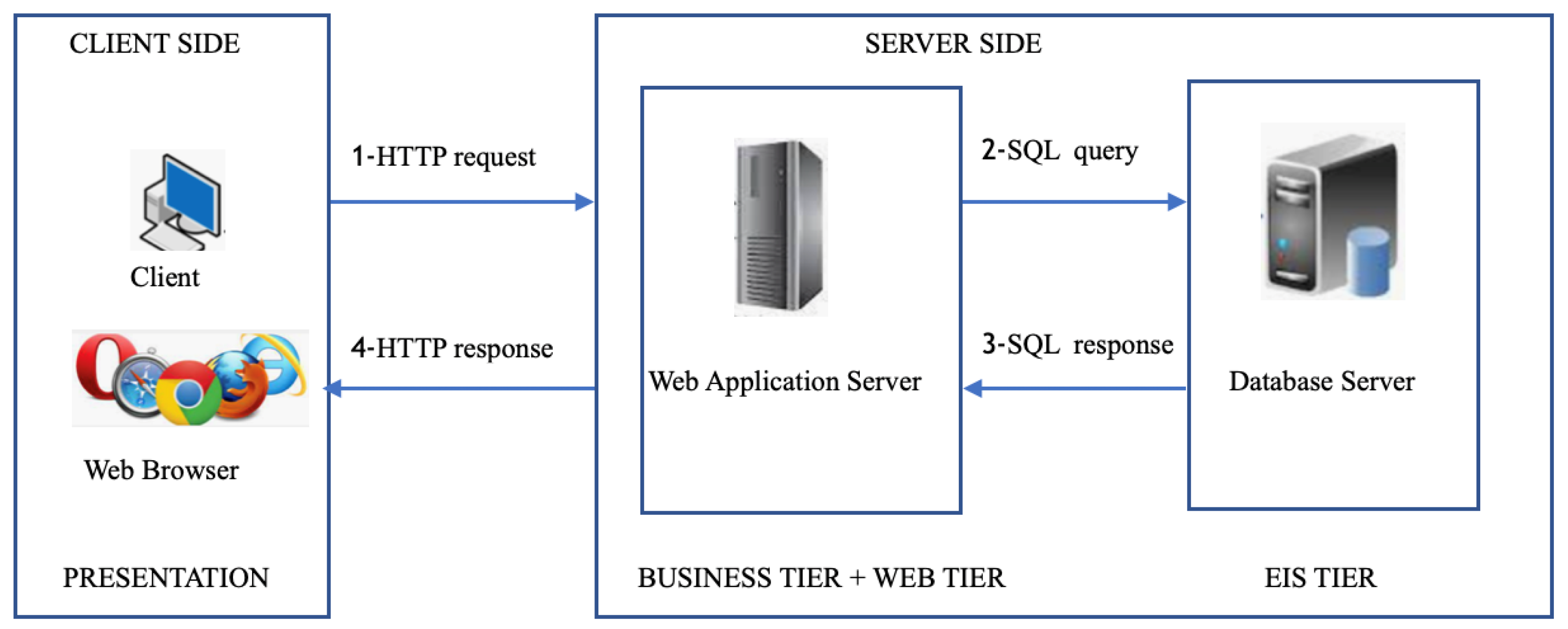
Future Internet | Free Full-Text | Deep Learning for Vulnerability and Attack Detection on Web Applications: A Systematic Literature Review
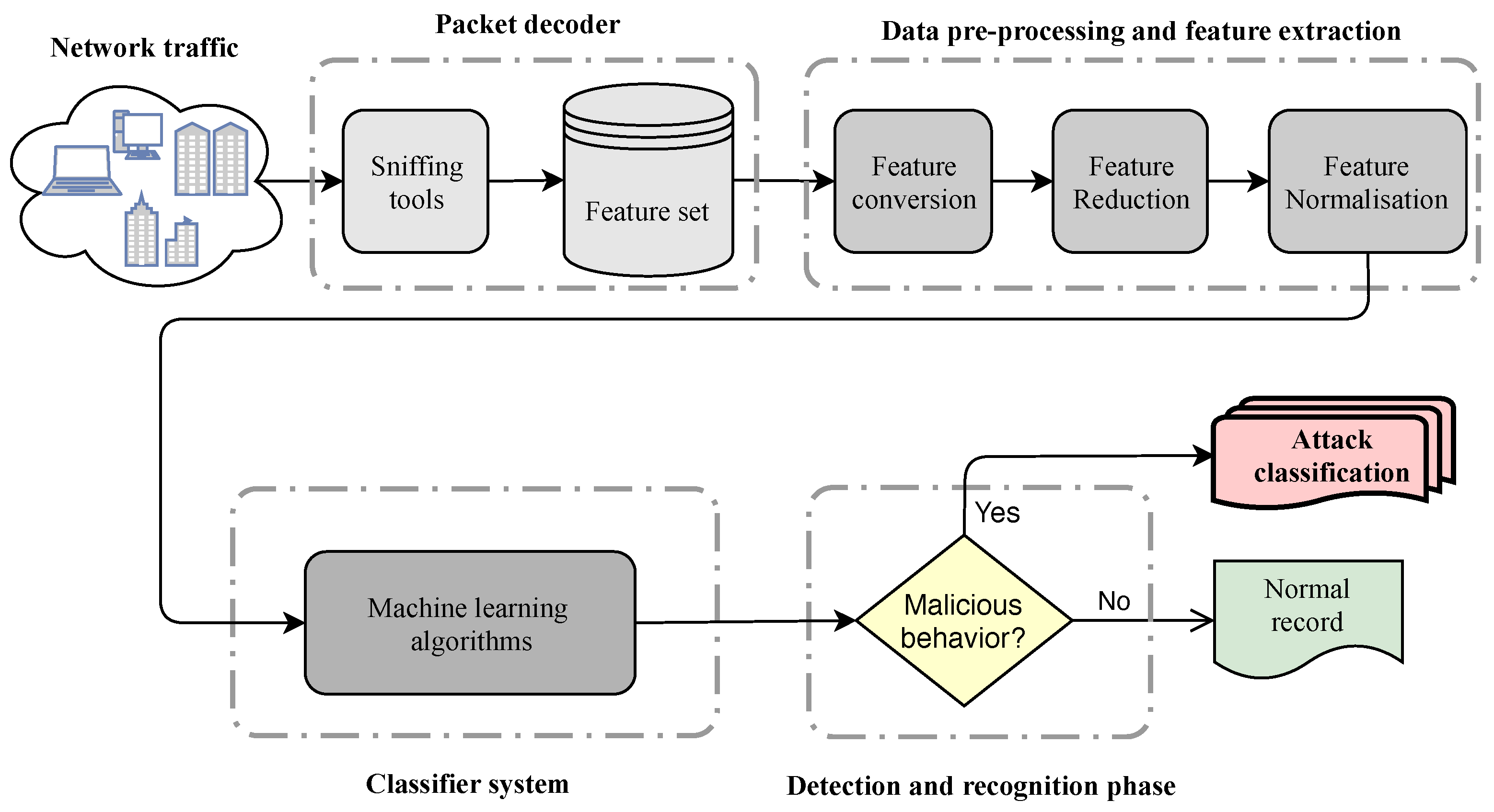
Entropy | Free Full-Text | A Review on Machine Learning Approaches for Network Malicious Behavior Detection in Emerging Technologies
Automated Malware Analysis Report for 607435844A556139638120B29A52C36AF59F9394.zip - Generated by Joe Sandbox
Unknown command" error when trying to debug a python script on open folder context · Issue #4070 · microsoft/PTVS · GitHub

Reverse Engineering Adventures: Brute-force function search, or how to crack Genshin Impact with PowerShell | Katy's Code
Artificial Intelligence and Machine Learning in Cybersecurity: Applications, Challenges, and Opportunities for MIS Academics


![PDF] PDF-Malware: An Overview on Threats, Detection and Evasion Attacks | Semantic Scholar PDF] PDF-Malware: An Overview on Threats, Detection and Evasion Attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f6fd3f88d2aa6959b042dc92c22719243e48404a/4-Figure4-1.png)






