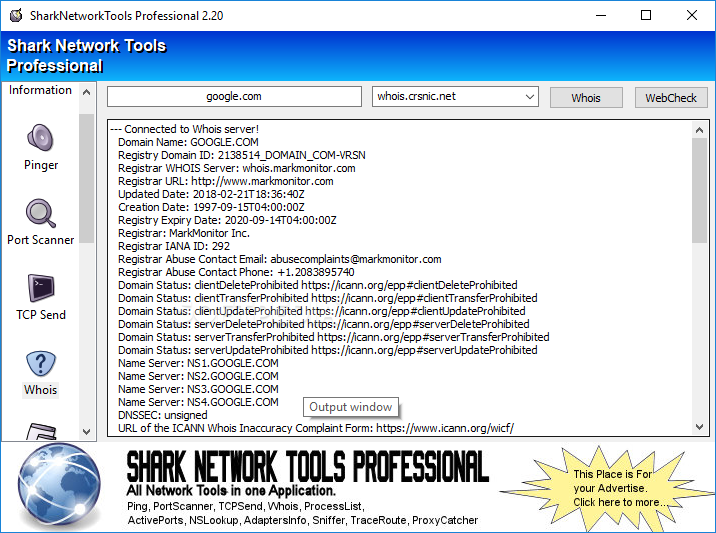
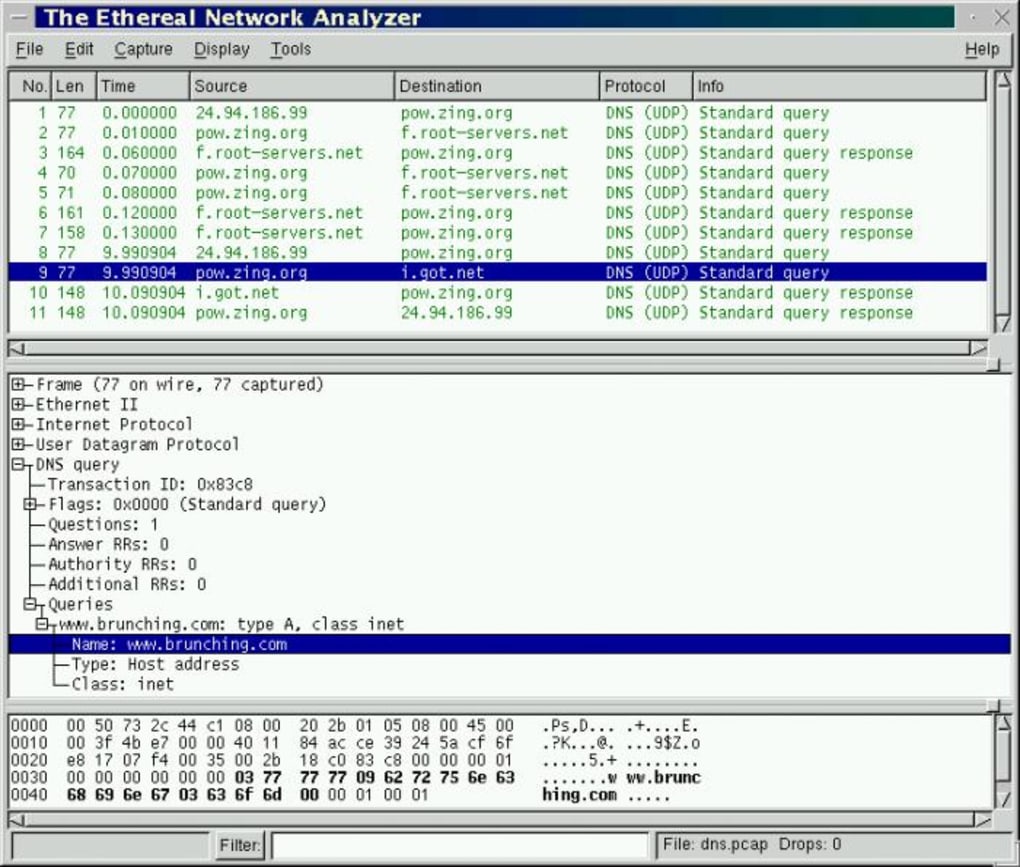
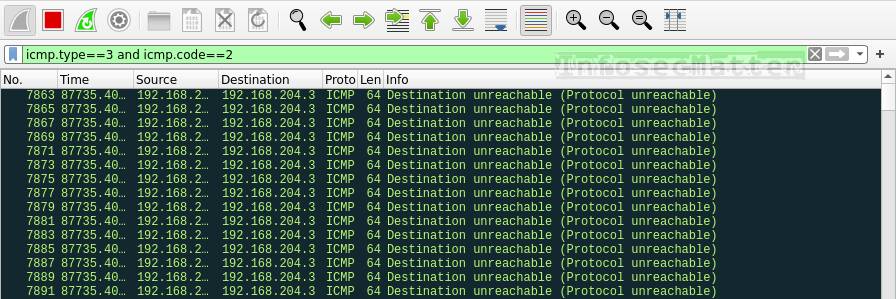
Network Services and Protocols Part II: How to Use Wireshark, Windows Firewall, and Advanced IP Scanner for Troubleshooting | by Bryan Renzy | Medium
Productivity 1000, Fanuc R30iA, and Ethernet/IP Scanner. How do I get the scanner to start sending network data?